Data breaches aren’t rare anymore — they’re simply part of the background hum that underlies our digital world.
Chances are, you’ve already been caught in the complicated web of one.
Maybe you even got an email from a company saying your data was exposed. And even if you didn’t, that doesn’t mean you were spared. It just means that no one told you.
Even if you’re super careful online, your information can still end up in the wrong hands, but you’re not helpless.
You can protect yourself right now.
Understand how data breaches affect people today, learn what personal details you should focus on protecting, and follow our steps to secure your data from being compromised.
It’s all below.
The Impact of Data Breaches Today
A data breach occurs when someone malicious (usually referred to as a “bad actor”) gains unauthorized access to sensitive information they shouldn’t have access to. They do this via hacking or finding a “backdoor” into a less-than-secure data storage system.
Data breaches can lead to identity theft, fraudulent account creation in your name, account takeovers, and ransom threats. Hackers may steal financial info or use your personal details to conduct phishing scams, where they craft emails that look convincingly real to trick you or someone you know into giving up money or sensitive details.
The fallout from a data breach can include lost money, damage to your credit score, harm to your reputation, and the daunting task of rebuilding your digital accounts from scratch.
As more of our personal data is stored online and AI-powered technology makes it easier to create nefarious data-farming programs, these breaches are becoming more powerful and prevalent!
A data breach isn’t just an abstract concept that happens to big businesses and folks with tons of assets to loot.
Even if you aren’t aware of it, you’ve likely been impacted by someone meddling with your personal information.
Take, for example, the 2024 cyberattack on the massive health payment processing company Change Healthcare, called “the most significant and consequential incident of its kind against the [U.S.] health care system in history” by Rick Pollack, President and CEO of the American Hospital Association.
The hacker group stole this data to collect ransom on it, which delayed medical care for millions of people and put many smaller medical practices in danger of closing due to lost revenue.
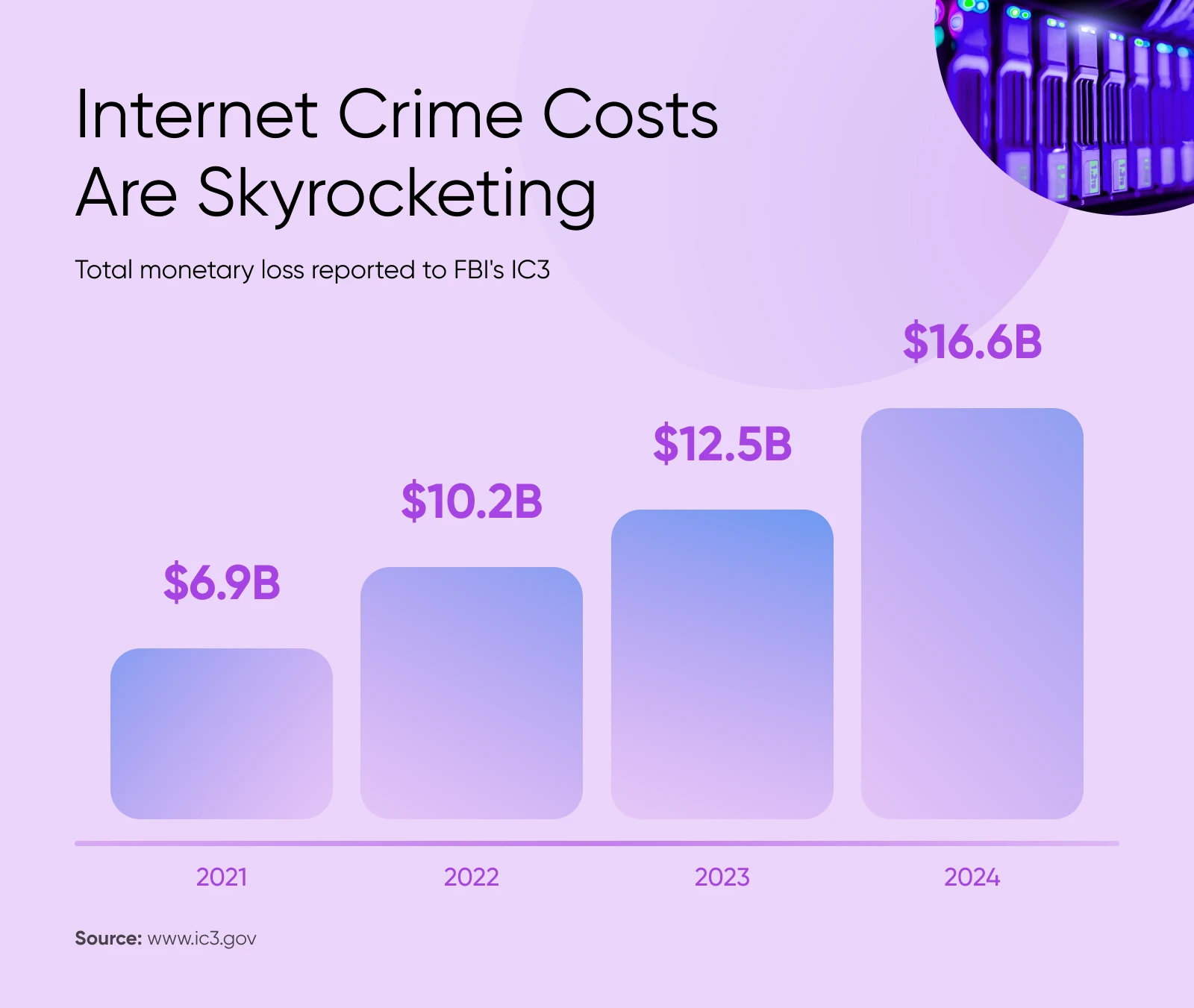
According to the FBI’s Internet Crime Complaint Center (IC3), where hundreds of thousands of individuals document cyber crimes annually, data breaches were one of the top complaints in 2024. And total monetary loss due to internet crimes continues to grow by leaps and bounds.
What Personal Data Do I Need To Protect?
Every time you use an app, visit a website, or even post on social media, you’re likely sharing small pieces of personal information that needs to be protected.
This can include things like…
- Your full name
- Your passwords
- Your social security number
- Your birthday
- Your location
- Your medical info
- Your relationships
- Your internet history
- Your device details
- Your browsing habits
How does this happen?
Often, you share information like this when you create an online account or make a payment. In addition, many companies collect this data using cookies and trackers to provide personalized advertising and experiences in return.
16 Ways To Safeguard Your Personal Data on the Internet
No matter whether you’ve shared information intentionally or it’s gathered quietly in the background by the tools you use, here are 16 tips you should implement right now to protect your personal data to the best of your ability.
Limit What You Share
An easy place to start is tobe mindful of the information you put online. Only share necessary personal information.
The less data you make publicly available, the harder it is for hackers and data brokers to exploit you.
Develop Different Identities for Online Use
Consider sharing different amounts or types of information depending on what you’re doing online.
While your bank does need to know a lot of information about you, does a social media site really need your full name, email address, and birthday?
Coming up with a few personas with varying degrees of detail and accuracy can help you limit how much sensitive information you share and better control which sites get a portrayal of your full identity.
Evaluate Every New Account
Sometimes, you can almost see a data breach coming when you consider a company’s practices, origins, and business model.
Not all apps and platforms will handle data responsibly. Determine how much you trust a new service you’re signing up for with these tips:
- Look for user reviews in the app store, on Reddit, and on YouTube.
- Check out the privacy policy. It should be easy to find, straightforward, and include contact information for the company.
- Consider how the platform makes money. If it’s free, what are they selling (your contact information, your behavioral data, etc.) to turn a profit?
- Consider the area of origin. Businesses outside your state or country could have lax security regulations.
- Does the URL in the address bar contain “https” and a lock icon? This ensures its TLS certificate is up to date, making it more likely to be secure and above board.
- Notice a sudden uptick in spam? That could be linked to information you’ve recently shared with a new platform.
Know Thy Enemy
Stay up to date on what kinds of organizations and people are out there gathering data, how they’re currently using it to conduct scams, and what best practices security professionals recommend.
Use a VPN When in Public
Public Wi-Fi is notoriously vulnerable to hackers. A VPN is a service you can subscribe to that encrypts your internet connection, keeping your data safe even when your connection is less than private.
Be sure to use it on all devices when accessing public networks!
Don’t Ignore Those Update Reminders
Sure, it’s easy to just click away those little security update pop-ups that always seem to arise when you’re right in the middle of something. Avoid the temptation!
Install updates for your operating systems, apps, and devices promptly to protect against the latest threats. These updates aren’t always just about implementing cool new functionality; they often also include critical security patches.
If your device has a setting to automate the update process, we recommend turning that on so you don’t even have the chance to forget.
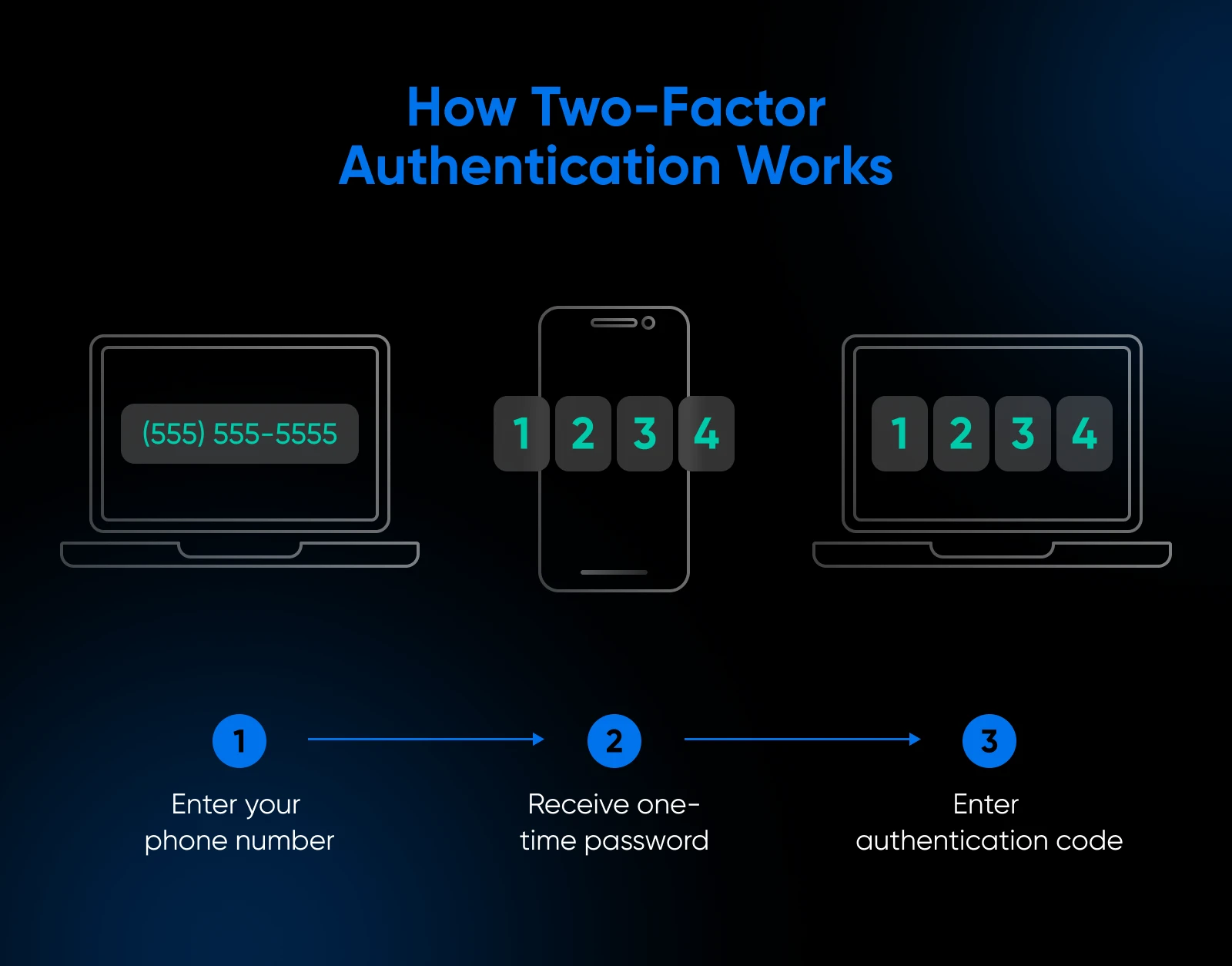
Set Up 2FA
Two-factor authentication (2FA) adds an extra layer of security by requiring a code or verification that’s sent to another account or device — all in addition to your password.
Even if someone steals your password, they can’t access your account without the second factor. Aside from strong passwords, 2FA is one of the simplest and best ways to show hackers you’re no easy target.
Limit Big Tech’s Access to Your Life
It’s probably no surprise that Amazon collects a huge amount of data about your shopping habits. The only way to fully escape its tracking is to stop shopping there entirely, but you can still take steps to reduce how your data is used.
For example, you can prevent Amazon from using your data for personalized ads. And if you use the Alexa service or any Amazon-owned devices (such as Kindle), you can change what kind of information those collect.
This article makes the process easy.
Click Discriminately
Avoid clicking on pop-ups, texts, links, and attachments —or anything that you don’t recognize, weren’t expecting, or were sent from a questionable source.
Phishing scams often send you things to click on that collect information in the background, or direct you somewhere else where they’ll try to gather it from you willingly. With the prevalence of these kinds of attacks on the rise, think twice before interacting with anything you’re sent digitally.
Consider Your Browser
Many of us just default to the browser that came installed on our devices. However, another way to sidestep data breaches is to use a privacy-focused browser. Firefox is a popular option that’s known for minimal data collection. Other options include Brave and DuckDuckGo.
Next, be sure to clear your browsing data regularly, including cookies, cached files, and saved permissions. And check your permissions to turn off access to your location, camera, and microphone. You can turn them back on manually should you need them.
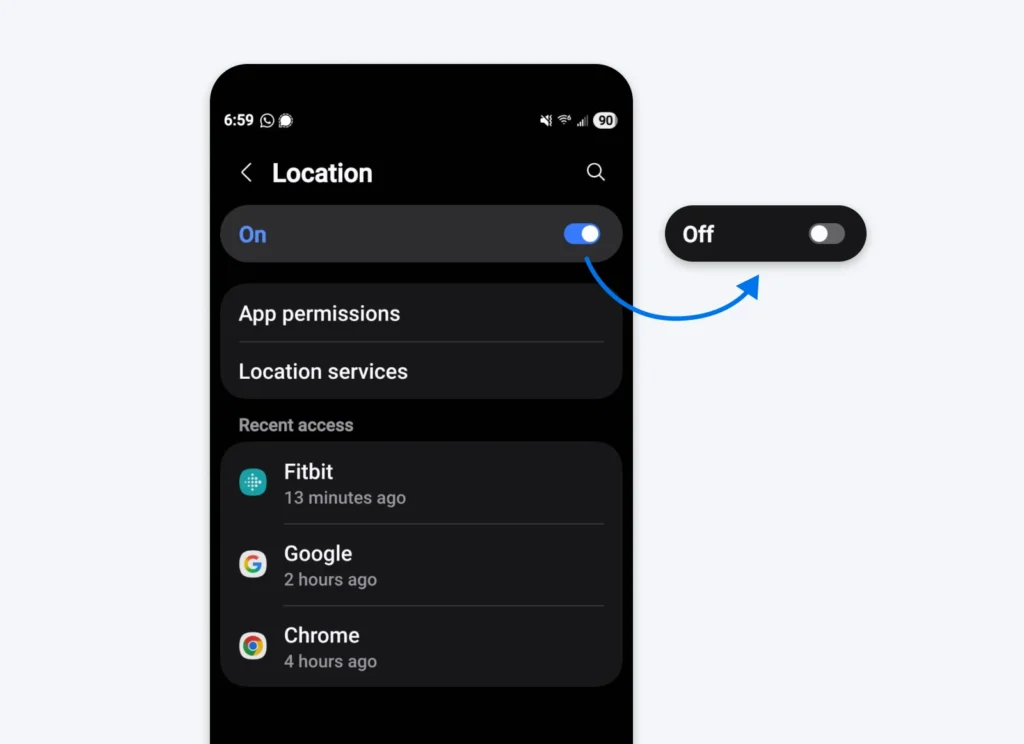
Stop Sharing Your Location Everywhere
Many mobile apps share your location data directly with third parties or to auctions where the information can be bought for advertising. If that wasn’t spooky enough, data brokers know this. They participate in those auctions and underbid just to secure general location information without even paying for it.
Avoid this by turning off location sharing on all of your devices and on each app you’ve downloaded. Again, you can turn this back on selectively as needed.
Go Dark(er) Online
Social media accounts are a major source of personal data collection. Adjust your profile settings to stay as private as you can, and be aware that any information you choose to share could fall into unknown hands.
Avoid engaging with messages from people you don’t know or trust. And don’t be afraid to use those block and report buttons if something feels fishy!
Stop Tracking in Its Tracks
Most websites use hidden tracking codes (aka cookies) that collect data about your activity. Blocking these cookies can prevent your information from ending up with advertisers, data brokers, and scammers.
This guide will get you started on blocking cookies on some of the most popular browsers.
You can also boost protection with privacy-focused browser extensions that block trackers automatically. Some popular options include Privacy Badger and uBlock.
Scrub Your Information From the Internet
Have you ever just Googled your name, or any name,and been shocked at all the info you can find?
The sites that show up in those searches — for example, Intelius, Spokeo, and BeenVerified — are all data brokers that collect personal information and make it way too easy for scammers and spammers to access.
Luckily, you can submit opt-out requests to reduce your visibility on these sites. But don’t forget to check back periodically. Your data can be added to these sources again as they continually scrape the web to compile profiles on individuals.
Check out the hilariously-named Big Ass Data Broker Opt-Out List to prioritize how you tackle this project.
Clean Up Your Apps and Accounts
This one’s simple: Delete apps and accounts you no longer use. Abandoned accounts that no one is checking on and unfinished security updates are prime targets for hackers.
To identify long-forgotten profiles, check out what you have saved in your password manager. You can also search your email inbox for phrases like “new account,” “new password,” or “welcome,” to find old or forgotten accounts.
Remember, deleting an app from your phone or computer doesn’t usually delete your account! Go the extra mile and clean up those accounts to reduce the amount of personal information that’s floating around out there just waiting to get scooped up.
Don’t Forget Other Connected Devices
Finally, gaming consoles, smart speakers, and even home appliances like your fridge can collect sensitive data if they’re connected to the internet.
Review the privacy settings on all of the above items in your home, and limit unnecessary data sharing and collection.
What To Do When Your Data Gets Compromised
Today, data breaches aren’t a matter of if — they’re pretty much a matter of when.
Knowing how to respond quickly by following these tips can protect your finances, identity, and digital life.
Assess the Actual Risk
The first step is understanding what information was exposed. Not all breaches are equally dangerous.
For example, if only your name and email were stolen, you might just see more spam.
But if sensitive data like your social security number or financial institution login were compromised, the risk of identity theft and fraud skyrockets.
Notifications from companies often tell you exactly what was affected. You can use that information to decide how many of the following tips you want to do.
Set Up Fraud Alerts on Your Credit
You can request a fraud alert from any of the three major credit bureaus (Experian, TransUnion, and Equifax).
This alert warns lenders that you may be a victim of identity theft, so they should take extra steps to confirm you are who you say you are before approving any credit in your name.
When you activate an alert with one bureau, it helpfully automatically applies to all three. Standard alerts last one year, with the option to renew.
Freeze Your Credit
Freezing your credit reports individually at each credit bureau stops anyone from accessing your credit file to open new accounts.
While a freeze provides excellent protection, it can, of course, complicate legitimate credit applications. If you need to do something like apply for a loan or open a credit card during this time, you can temporarily lift the freeze.
Hire a Data Removal Service
Specialized services can search the dark web for stolen personal information and attempt to remove it. The dark web is decentralized and anonymous, making manual removal nearly impossible for most people — hence why paid services like this exist.
While these services aren’t perfect, they can significantly reduce the amount of personal information you have floating around out there, reducing your risk of fraud or phishing.
Some of these services focus only on the regular web or data brokers, so make sure you choose one that covers the dark web if the sensitive or valuable information has been compromised.
Appeal to Above-Board Data Brokers
Outside the dark web, your information is most often at risk when it’s collected and sold by data brokers.
You can personally submit requests to these brokers to delete and not sell your data, or you can use a specialized data removal service to help handle it.
Compliance with your request will depend on the local laws of the data broker, but this step can still limit your data’s exposure and make it harder for scammers to access your information.
This article covers some good choices for data removal providers that scan the dark web, data brokers, and beyond.
Watch Your Payment Apps Closely
Digital payment apps like Cash App, Venmo, and Zelle often have weaker security than banks and credit card companies do. So if your data has been accessed anywhere, many criminals will make a beeline to these platforms to see if they can break in.
Keep an eye out for any nefarious use by enabling transaction alerts so you’re notified immediately of all activity.
Report unauthorized transactions as soon as possible. Scammers frequently test whether or not you’re paying attention by making really small transactions at first. If you catch fraudulent spending quickly, many payment platforms will even reimburse you.
Additionally, be sure 2FA and other available security measures are turned on within these apps.
Update All Your Passwords
After a data breach, one of the most important steps is to change your passwords.
Some people would recommend only updating the affected accounts, but we’d argue this is a good time to update everything — especially if you’ve reused passwords. If hackers gain access to just one account, they often try the same credentials on others.
Now is the time to create strong, unique passwords for every online account. Absolutely avoid using the same or similar passwords across multiple sites.
Worried you won’t be able to remember them all? Consider using a password manager to generate and store complex passwords securely. Then, all you have to do is remember how to log into that one site.
If you don’t know where to start, focus first on accounts that are rich with sensitive information, like email and banking.
Stay Sharp!
After a data breach, hackers often use the information to launch targeted phishing attacks.
They can impersonate legitimate sources such as your bank, government agencies, or even friends to trick you into sharing more sensitive info.
Watch for these common signs of phishing:
- Urgent messages pressuring you to act immediately
- Email addresses and language that looks unusual, even if it’s just slightly off
- Unexpected attachments
- Requests for sensitive information or details that the requester should already have, like account numbers, addresses, and names

FAQs About Data Breaches
What is a data breach?
A data breach occurs when unauthorized parties gain access to sensitive information, such as passwords, financial data, or personal details.
How do I know if I’ve been affected by a data breach?
Expect a notification if a company discovers that your information was collected in a recent cyber attack. However, this isn’t a failsafe. Your data could still be compromised without your knowledge.
What personal information is most at risk in a data breach?
Commonly targeted information includes passwords, social security numbers, credit card data, medical records, and behavioral data like browsing and purchasing history.
What should I do immediately after a data breach?
Assess the type of data exposed to understand how carefully you need to clean up, update passwords, enable 2FA, set up fraud alerts and/or credit freezes, consider data removal services, and continuously monitor accounts for suspicious activity.
Stay Safe Out There
Data breaches are inevitable in today’s digital world, but that doesn’t mean you’re powerless.
By understanding what personal information faces security risks and taking proactive steps — like controlling your online footprint, using strong security practices, and responding quickly after a breach — you can reduce your exposure and protect yourself from the worst consequences.
Did you enjoy this article?




